AppSec That Scales Faster Than AI Can Generate Code
Deterministic remediation, runtime threat modeling, and preventative guardrails for modern software teams.
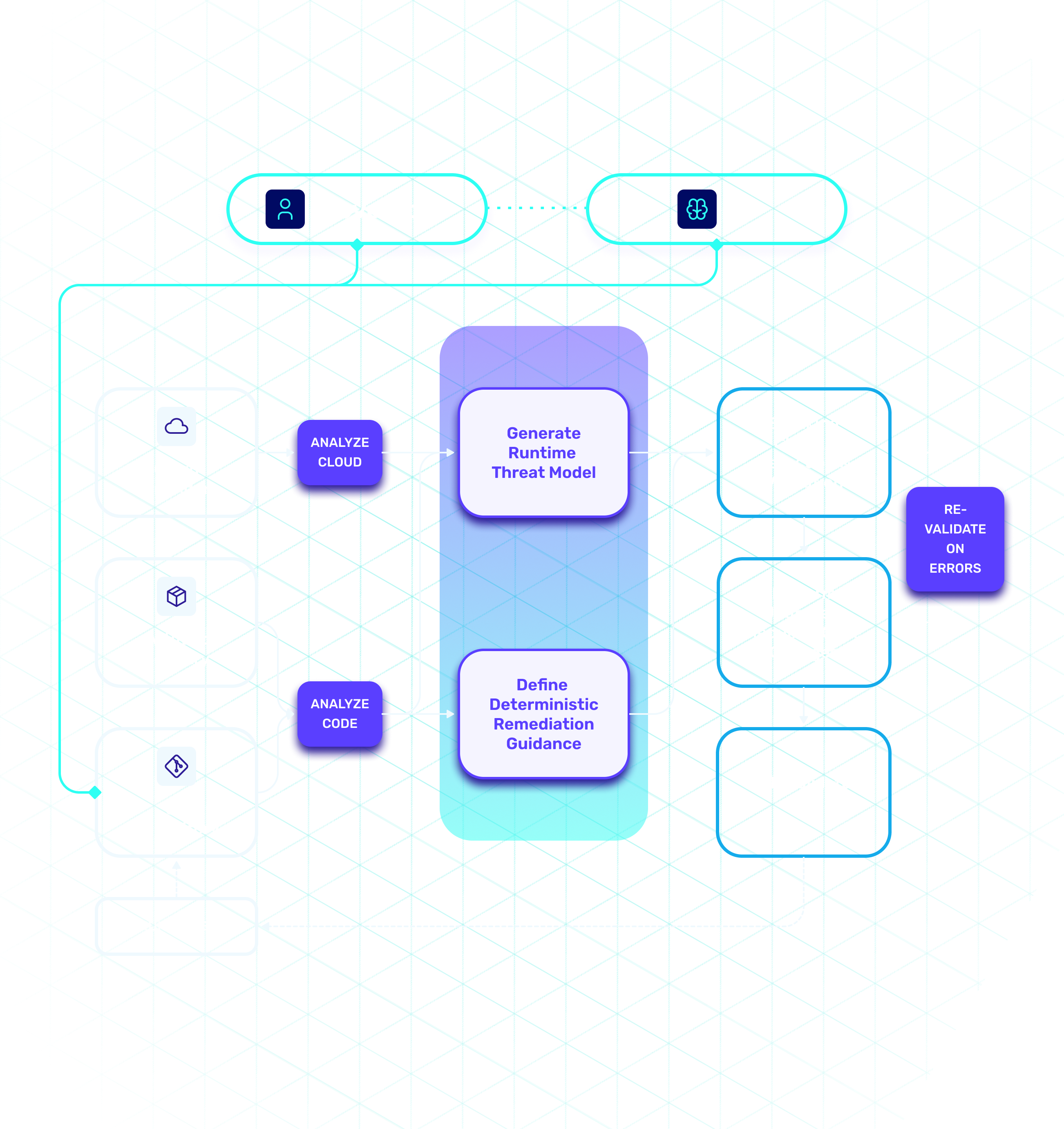
Co-pilots assist. Agents guess. Heeler fixes for you.
Deterministic AppSec Agentic Remediation
Remove Remediation Paralysis
Heeler autonomously investigates dependency upgrades and prepares merge-ready PRs, only when fixes can be fully validated. Deterministic analysis identifies breaking changes and the safest upgrade path, applies required code changes, and verifies them against compilation and unit tests. Developers stay in control. No prompts. No hallucinations.
Prevent New Security Debt
Heeler enforces security and hygiene rules before code is committed and on every pull request, catching problems early and automatically fixing them so risk and technical debt never pile up again.
Focus on Real Risk
Heeler builds a living model of your applications by connecting repositories, services, and infrastructure. This runtime model enables Heeler to analyze how vulnerabilities could actually be exploited and prioritize remediation based on real-world impact.
2 weeks
Saved Annually for Every Developer
70% +
Reduction of Security Debt
95%
Noise Reduction
15 min.
Time Required to Deploy Heeler
What Makes Heeler Different


Prioritize Vulnerabilities Based on Exploitability and Business Impact
Focus on vulnerabilities that are actually exploitable in your environment. Heeler’s runtime threat modeling engine analyzes how code runs in production to generate business-aware attack paths—helping you prioritize what matters.
Runtime Library Reachability
Service-to-Service Relationships
Internet Accessibility
Analysis of Static and Runtime Mitigations
Business Impact
Environmental Boundaries
Level of Compromise
Threat Likelihood


Remediation Guidance Developers Can Act On
Heeler delivers contextual remediation guidance that identifies the safest upgrade paths, flags breaking changes, and analyzes library upgrade impact. Developers save hours of manual research, making fixes faster, safer, and less disruptive to their workflow.
Calculates the Safest Upgrade Path
Dependency Graphs
Detects Breaking Changes Automatically
First-Party & Transitive Coverage
Provides Human-Readable Upgrade Guidance
Surfaces Fixable, High-Risk Issues First


Agentic Remediation: Automating Library Updates
Agentic workflows leverage language intelligence and post-compilation checks to generate validated PRs for remediation and hygiene updates. Automating resolution of security debt while freeing developers to focus on high-impact features—strengthening both developer velocity and security resilience.
Generates Validated PRs for Upgrades
Multi-Step Agentic Validation of PRs
Calculates Best Upgrade Path
Supports First-Party Library Upgrades
Handles Transitive Dependency Upgrades
Performs 1st Party Code Changes


Shift Dependency Enforcement Left—with Runtime Context
By enforcing policies at the pull request level with runtime-aware context, Heeler enables teams to block or flag risky dependencies before they hit production—ensuring protection against known high-risk libraries at the earliest stage possible.
Enforces Granular PR-Level Policies
Runtime-Aware Decisioning
Blocks Known Risky Dependencies Pre-Merge
First-Party & Transitive Coverage
Supports Tiered Enforcement (Block, Flag, Allow)
Progress Tracking


Code-to-Cloud Without the Overhead
Read-only connections into your repos and cloud service providers is all Heeler needs. No agents, build modifications, tagging, or pipeline integrations required. Using a patent-pending process Heeler correlates deployed compute back to specific changesets (not just repos), even within complex monorepos, while automatically capturing environmental context.
No Agents, or Build or Pipeline Modifications
Works Seamlessly with Complex Monorepos
Real-time Architecture Diagrams
Captures Full Environmental Context Automatically
Links Exact Changesets to Deployments
Maps Service Relationships and Dependencies
.svg)





.jpg)
